Manage Runtime Permissions and AppOps on new Firmware with support of SDK v1.34.4 and Scan2Deploy Studio
Since its born Android included a per-app permissions system, bases on a Manifest Files, where each app had to declare, to the system and to the user, which special device feature (like camera, position, networking and many other) wanted to use.
The list of permissions has grown over the years, and hand in hand with the number of applications installed on devices, their management has become increasingly complex for developers and the user.
Over time Android has always adjusted and improved its model, grouping and modifying permissions best protect the privacy of the data.
Starting from Android 6.0, all these permissions are associated to a protection level based on the nature of the resources to which the permission gives access to. Whether or not a permission is granted to an application depends on the level of protection associated with the specific permission requested. Possible values are:
normal: is the value that, if no protection level is indicated, is set by default. It is used for all those permissions that are not used to perform critical operations on resources. These permissions are automatically granted to the application, and do not require explicit confirmation by the user.
dangerous: Permissions with level dangerous generally allow you to control the device or the data on it in some way. Unlike other permissions, these are not automatically granted to the app requesting them. If an app declares that it needs a permission listed as dangerous, the user must explicitly grant the permission to the app; the app must show, at runtime, a warning to the user, who may or may not accept it. As of API version 23 (Android 6.0), the user can also revoke, at any time, the permissions previously granted to the app. The app. then, whenever it wants to use them, will have to check the permissions.
signature: a signature level permission is granted only to those applications signed with the same key as the application that defines permissions.
You can grant or revoke only runtime permissions declared in the application manifest, with protection level dangerous and, either from device GUI (Settings menu) or CLI (adb shell):
adb shell pm grant [--user USER_ID] <PACKAGE> <PERMISSION>
adb shell pm revoke [--user USER_ID] <PACKAGE> <PERMISSION>
In addition to dangerous permissions, it's also possible to grant or deny or ignore a set of other special permissions shown under:
Settings → Apps & Notifications → Advanced → Special App Access.
All of these are not managed directly by the Package Manager (pm), but by Application Operation (appops), a secondary framework for controlling permissions.
These are signature-level permissions that can only be granted to system applications.
To either deny or allow an “AppOps” permission for a that app through adb you can use:
adb shell appops set [--uid] <PackageName> <PermissionName> ignore
adb shell appops set [--uid] <PackageName> <PermissionName> deny
adb shell appops set [--uid] <PackageName> <PermissionName> allow
In the enterprise environment, managing these types of permissions and appops on large fleets of devices requires tools for staging and automating these configurations.
To provide an automation method for granting the runtime dangerous permissions, starting from SDK 1.25 (see FWs compatibility table at Datalogic Android SDK | Technical Documentation), Datalogic introduced a new AppManager class that allows third party apps to programmatically grant single or multiple runtime permissions required by the applications, through two new class methods: grantPermissions(<package>,<permissions>) and grantAllPermissions(<package>).
This is an example on how use the grantAllPermissions():
val am = AppManager(application.applicationContext)
ret = am.grantAllPermissions(this.packageName)
In the same way, starting from the new FW releases supporting SDK 1.34.4 (see FWs compatibility table at Datalogic Android SDK | Technical Documentation), Datalogic also whitelisted Scan2Deploy Agent to allow the execution of SHELL scripts containing the appops command. The most recent FW for Memor 11, Skorpio X5, Memor 20 already support the new feature. The firmware for JoyaTouch 22 will support it soon.
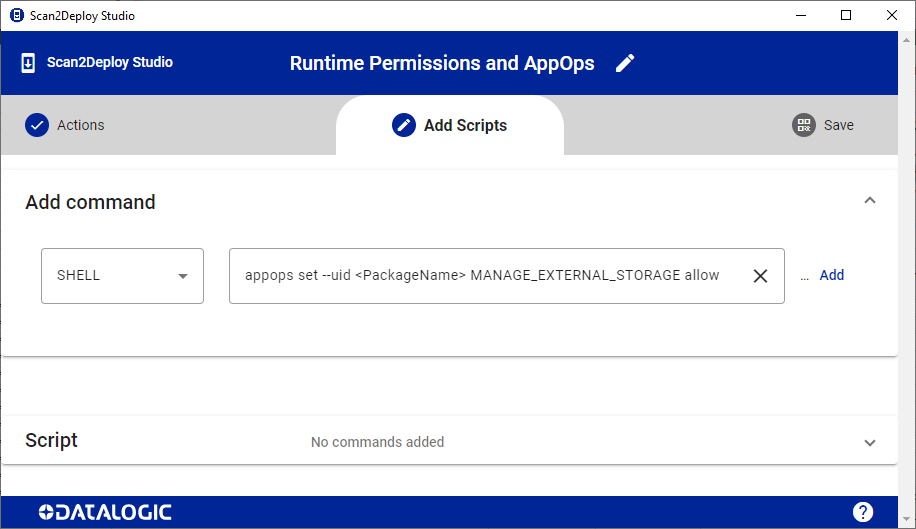
This is an example on how to allow MANAGE_EXTERNAL_STORAGE appops to a package using Datalogic Scan2Deploy Studio:
SHELL --> appops set --uid <PackageName> MANAGE_EXTERNAL_STORAGE allow
List of devices and firmware that introduced the support for SDK 1.34.4 (September 22nd, 2023):
Skorpio X5 Android 11: fw3.21.001 released on 2023-08-28 | SDK 1.34.4
Memor 20 Android 11: fw3.22.001 released on 2023-08-28 | SDK 1.34.4
Memor 11 Android 11: fw1.03.07 released on 2023-09-31 | SDK 1.34.6
JoyaTouch 22 Android 11: fw1.13.02 released on 2024-01-15 | SDK 1.34.7.
Follow the topic on the Discussion Board: grantpermissions() APIs and appops permissions
---
create on: September 22nd, 2023

